Cybersecurity in the Railway Industry: Safeguarding the Tracks of the Future Part-1

Introduction
As a child, trains were my greatest fascination. Growing up near railway tracks, I spent countless hours watching trains come and go. One summer afternoon, my father, noticing my obsession, took me on a surprise trip to the nearby train station. A family acquaintance, Mr. Murari, a train pilot, invited us into the engine room. Stepping into that space was like entering a dream—controls, levers, and the engineer’s grease-stained overalls captivated my young mind. I even got to blow the train’s whistle, a sound that still echoes in my memory as a symbol of childhood wonder.
Fast forward to today, and the train’s allure remains strong for many, including myself. However, recent train collisions and incidents in Indian Railways have raised a new concern – could these complex systems be vulnerable to cyberattacks…? This question has driven my research and forms the foundation of this blog.
The Evolving Landscape of Railways
Over the last decade, the railway industry has transitioned from a traditional, mechanical system to a highly digitized and connected ecosystem. Modern trains are now equipped with advanced digital systems for navigation, control, and diagnostics, enhancing both safety and passenger experience. Today’s passengers expect real-time updates, seamless mobile payments, and robust connectivity—demands that have accelerated the industry’s digital transformation.
However, this digital evolution also brings new challenges. The very technologies that make railways smarter and more efficient have expanded the attack surface, offering cyber-criminals more opportunities to infiltrate and disrupt critical operations.

Indicator Board, Eastwood Station, Sydney (2008)
For smaller stations which only had an up/down service pattern, these boards were pretty much ideal for quickly determining which platform the next train was leaving from and where it would stop.
The board on the far left shows a city-bound train leaving from Platform 3.
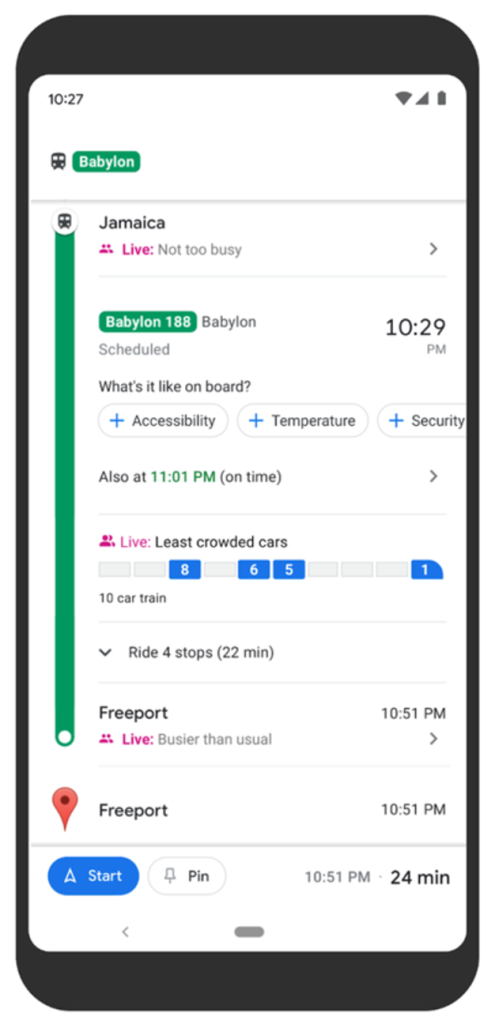
Google Maps has launched a new feature aimed at making people feel safe as they navigate public transport around the world.
The app has expanded its “transit crowdedness predictions” to more than 10,000 transit agencies in 100 countries, so users will be able to find out ahead of time if their chosen bus, train or subway is likely to have lots of free seats, has hit full capacity, or is somewhere in between.
With this information, pubic transport users can decide whether they want to hop on board or wait a while. “Because, pandemic or not, no one likes standing in a jam-packed subway car,” says Google.
Cybersecurity Challenges in Railways
Modern signaling and train management systems (TMS) are at the heart of today’s railway operations, enabling more trains to run safely and reliably. These systems are rich in connectivity, utilizing wireless technologies that propel the industry into the future. But from a cybersecurity perspective, this connectivity is a double-edged sword. The increased attack surface poses significant risks, with future technologies likely to amplify these vulnerabilities.

Electrical Mechanical Signalling System now part of of Bangalore Division’s history.
“It is vintage by Railway standards,” said Divisional Railway Manager, Bangalore Division, Akhil Agrawal. “Equipment used for operational purposes are generally changed every 25 years due to wear and tear. We are fortunate that this machine was used for more than 40 years and it functioned perfectly well till its last day,” he said.
Preventive maintenance analytics, real-time data, augmented reality, and even robots and drones are revolutionizing railway maintenance and operations. While these innovations promise significant benefits, they also present new opportunities for attackers seeking to damage infrastructure or cause service disruptions.
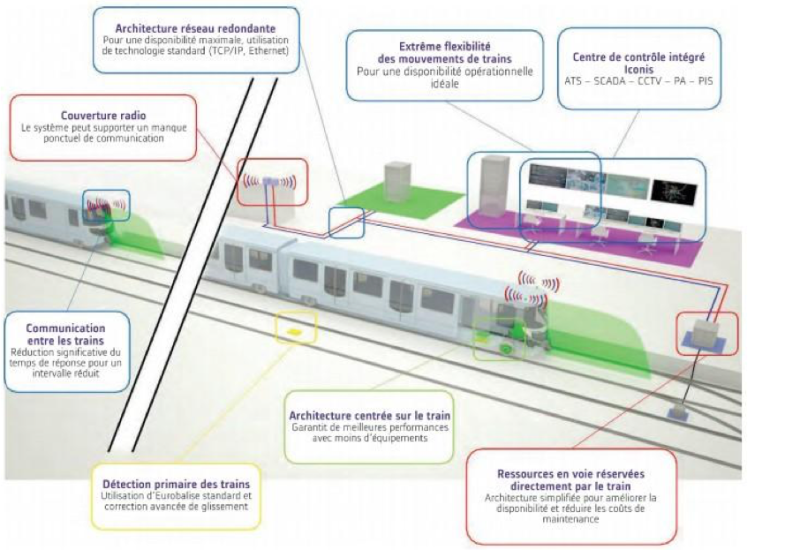
PC – https://www.bureauveritas.fr/magazine/alstom-revele-les-secrets-de-ses-trains-du-futur
What’s at Stake?
A successful cyberattack on a railway network could have severe consequences:
- Loss of Confidence: Even a minor cyber incident could erode public trust, causing passengers to choose alternative modes of transport. This business concern, while seemingly minor, could have long-term financial impacts.
- Loss of Sensitive Data: Beyond IT and business operations, sensitive data in railway networks could include critical firmware for signaling devices. If compromised, this data could enable further attacks on the same or other networks.
- Decreased Availability: Denial of Service (DoS) attacks could lead to delayed or halted trains, resulting in dissatisfied passengers and potential fines for operators in some countries.
- Damage to Infrastructure: Cyberattacks could disable critical equipment, such as smart interlocking systems, leading to extended service outages or even physical damage to railway infrastructure.
- Threat to Human Lives: The most concerning consequence is the potential for fatalities. While the railway industry’s strong safety culture mitigates many risks, a successful cyberattack could still compromise safety in catastrophic ways.
Loss of Confidence
Passengers losing trust into transport system
Loss of Sensitive Data
Operational Data & Sensitive IP
Decrease of Availability
Leads to costly downtime & client dissatisfaction
Damage to Infrastructure
Impact to IT/OT infrastructure
Fatal Safety Incidents
Cyber-attacks compromising the safety-case of your “crown-jewel”
Real-World Examples of Cyberattacks on Railways
The growing frequency of cyberattacks on railway systems is a stark reminder of how critical these infrastructures are—not just for daily transportation but as strategic assets in global conflicts. As railways become more digitized and interconnected, they present an increasingly attractive target for state-sponsored actors and sophisticated cybercriminals. The following examples illustrate the significant role that railway cyberattacks can play in the broader context of international conflicts and the future of warfare.

- Denmark Train System Halted by Cyberattack (November 2022)
In a significant incident, Denmark’s largest train operator, DSB, was forced to halt all operations due to a cyberattack on its IT service provider, Supeo. The attack highlights the vulnerability of critical transportation infrastructure to disruptions through third-party suppliers. In the event of a geopolitical conflict, such attacks could be used strategically to paralyze a nation’s transportation, causing widespread chaos and undermining public trust in the government’s ability to protect essential services. https://www.securityweek.com/cyberattack-causes-trains-stop-denmark/ - Ransomware Attack on Italy’s State Railway (March 2022)
The Italian state railway, Ferrovie dello Stato Italiane, experienced a ransomware attack that crippled its ticketing system, preventing customers from purchasing tickets. More alarmingly, the attack later extended to operational technology (OT) systems, including signaling networks. This kind of attack on critical infrastructure could easily be weaponized in a conflict, where disrupting transportation can cripple a nation’s economy and mobility, significantly affecting military logistics and civilian morale. https://www.railsistem.com/blog/2023/10/27/railway-cybersecurity-the-rising-threat-to-signalling-systems/ - Cyberattack on Belarus Railways Amid Russia-Ukraine Conflict (2022)
During the early stages of the Russia-Ukraine conflict, Belarus’s railway control systems were targeted by hackers. This cyberattack was part of a broader strategy to disrupt the movement of Russian military supplies, showcasing how railway systems can become battlegrounds in modern warfare. The attack on Belarus’s railway infrastructure exemplifies the potential for cyber warfare to influence the outcome of physical conflicts without direct military engagement. https://www.cylus.com/post/on-the-right-track-5-rail-cybersecurity-predictions-for-2023 - Germany’s Deutsche Bahn GSM-R Attack (2022)
Northern Germany’s Deutsche Bahn faced a dual attack—both physical and cyber—on its GSM-R communications infrastructure. This incident disrupted train services and underscored the dual-threat nature of modern conflicts, where critical infrastructure is targeted to create economic and social instability. The GSM-R system, vital for train signaling and communication, represents a critical vulnerability in the railways, which, if exploited during a conflict, could lead to catastrophic disruptions https://www.railsistem.com/blog/2023/10/27/railway-cybersecurity-the-rising-threat-to-signalling-systems/
These examples highlight the increasing significance of railway systems as targets in both peacetime and wartime scenarios. As geopolitical tensions rise, the cyber domain has become a new front where nations can assert power and inflict damage without direct physical confrontation. Railways, due to their critical role in national logistics, economy, and civilian mobility, are particularly vulnerable. Disrupting railway operations can lead to immediate, widespread consequences, making it a powerful tool in the arsenal of state-sponsored cyberattacks.
In future global conflicts, cyberattacks on railways could be used to:
- Paralyze Military Logistics: Railways are key for the rapid movement of military personnel and supplies. Disrupting these networks could delay reinforcements and essential supplies, affecting the outcome of military operations.
- Undermine Civilian Morale: Interruptions in public transportation during a conflict can cause panic, economic loss, and a loss of public confidence in government authorities, further destabilizing the affected nation.
- Exert Economic Pressure: Railways are vital for freight transport. A well-timed cyberattack could disrupt supply chains, leading to shortages and economic pressure on a global scale.
Continued in Part-2….
Disclaimer:
- The views expressed in this post are my own and do not necessarily reflect the views or positions of my organization.
- The names and designations of individuals mentioned in this blog have been changed to protect their privacy. Any resemblance to real persons, living or dead, is purely coincidental. The content and quotes provided are intended for illustrative purposes only and are based on common industry experiences and challenges.
