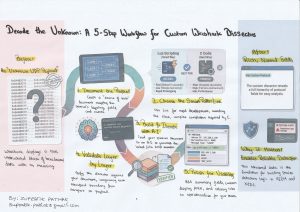
How to Decode “Unknown” Protocols in Wireshark
Wireshark is phenomenal—but your job doesn’t end where its built-in protocol list does. I’ve long been intrigued by how Wireshark turns raw bytes into a clean, hierarchical packet view. Understanding that mechanism—fields, lengths, tags, and how a dissector maps bytes to meaning—pays off far beyond packet analysis. It’s the same foundation you need to develop reliable detection logic in SIEM and NIDS: translate protocol semantics into precise match conditions, field extractions, and anomaly rules, instead of relying solely on signatures.















