Cybersecurity in the Railway Industry: Safeguarding the Tracks of the Future Part-2

The Complex Architecture of Modern Railway Systems
Modern railway systems are a sophisticated network of interconnected components that work together to ensure the safe and efficient movement of trains. These components, which include field elements, interlocking systems, trackside equipment, onboard systems, external networks, and Operation Control Centers (OCC), are all connected through Wide Area Networks (WAN) and wireless communication networks. Understanding how these elements interact is crucial for grasping the potential cybersecurity risks within this complex architecture.
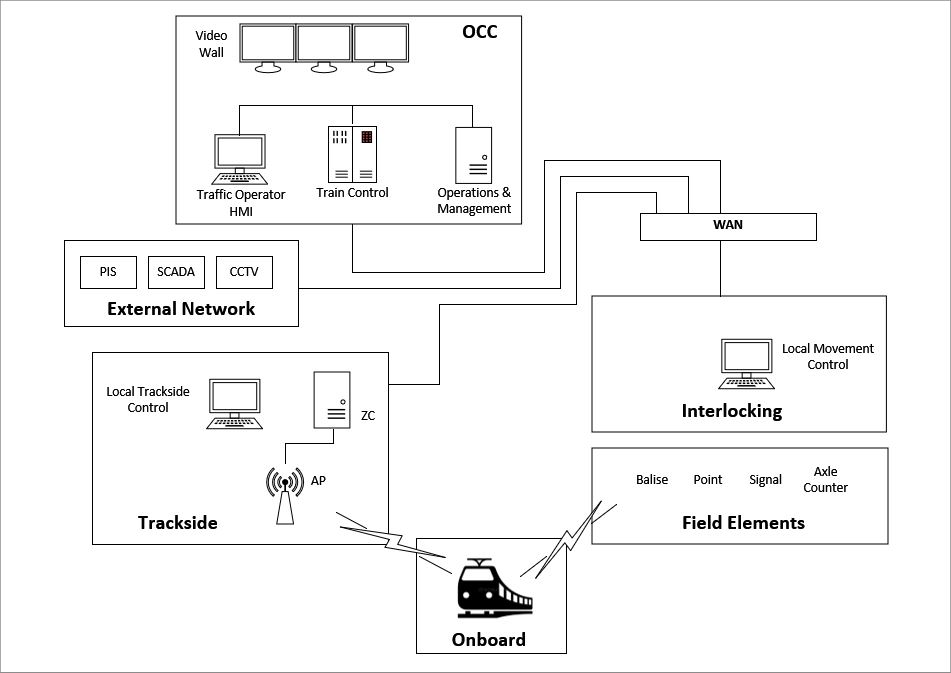
Field Elements
Field elements are the physical devices and infrastructure located along the railway tracks. These include sensors, switches, signals, and other trackside equipment that monitor and control various aspects of train movement. For example:
- Trackside Sensors: These sensors detect the presence of trains on the tracks, monitor track conditions, and provide real-time data to the control systems.
- Switches and Signals: These are used to direct train traffic, change track paths, and ensure that trains are operating on the correct routes.
Field elements are critical for maintaining the operational safety and efficiency of the railway network. However, because they are often spread over large distances and in remote locations, they are vulnerable to both physical tampering and cyber infiltration. Attackers could potentially exploit these elements to disrupt train operations by interfering with signals or manipulating track switches.
Interlocking Systems
Interlocking systems are a vital component of railway safety, designed to prevent conflicting train movements through the control of signals and track switches. These systems ensure that only one train can occupy a section of track at a time, thereby avoiding collisions.
- Smart Interlocking Systems: Modern interlocking systems are increasingly digitized, allowing for more efficient management and control of train movements. These systems are connected to a central control system and can be monitored and operated remotely.
Interlocking systems are particularly critical because any compromise could lead to catastrophic failures, such as train collisions. Cybercriminals targeting these systems could manipulate signal settings or track switches, creating unsafe conditions on the railway network.
Trackside Equipment
Trackside equipment refers to the various devices and systems installed along the tracks to support railway operations. This includes:
- Signaling Devices: These provide visual and electronic signals to train operators, indicating whether it is safe to proceed or if they need to stop.
- Communication Infrastructure: Trackside equipment often includes communication systems that relay information between trains and the OCC.
This equipment is essential for real-time communication and control but is also susceptible to cyber threats. For instance, an attacker could intercept or spoof communication signals, leading to incorrect instructions being sent to trains.
Onboard Systems
Onboard systems are the technologies installed within the trains themselves. These systems include:
- Train Control Systems: These systems manage the speed, braking, and direction of the train, ensuring that it operates within safe parameters.
- Passenger Information Systems (PIS): These provide passengers with real-time updates about their journey, including arrival times and station information.
Onboard systems are increasingly connected to external networks for real-time updates and control. However, this connectivity also introduces vulnerabilities, as attackers could potentially gain access to onboard systems and interfere with train operations.
External Networks
External networks encompass the various communication and data networks that connect railway systems to the outside world. This includes:
- Vendor Networks: Many railway systems rely on third-party vendors for maintenance, software updates, and system monitoring. These external networks are often integrated with the railway’s IT and OT systems.
- Public Communication Networks: Passenger information and ticketing systems often interface with public networks, such as the internet, to provide real-time services.
External networks are a significant point of vulnerability, as seen in cases where attacks on third-party vendors have led to widespread disruptions in railway services.
Operation Control Centers (OCC)
The OCC is the nerve center of railway operations. It is where all the data from field elements, interlocking systems, trackside equipment, and onboard systems are collected, monitored, and managed. The OCC is responsible for:
- Real-time Monitoring: Continuous oversight of train movements, signal status, and track conditions.
- Decision Making: Operators at the OCC make critical decisions based on the data received, such as rerouting trains, adjusting schedules, and responding to emergencies.
Because the OCC is central to railway operations, it is a prime target for cyberattacks. A breach of the OCC could lead to widespread disruption, as attackers could manipulate train schedules, interfere with signaling systems, or shut down the entire network.
WAN and Wireless Networks
The backbone of modern railway communication is the WAN and wireless networks that connect all these components.
- Wide Area Network (WAN): The WAN connects various subsystems, such as the OCC, interlocking systems, and field elements, across large geographical areas. It allows for the centralized control and monitoring of the railway network.
- Wireless Networks: Wireless communication is used extensively for real-time data transmission between trains and the OCC, as well as between trackside equipment and control centers. These networks enable the seamless operation of high-speed trains and the provision of real-time information to passengers.
While WAN and wireless networks are essential for modern railway operations, they also introduce significant cybersecurity risks. These networks can be susceptible to interception, jamming, or spoofing by cybercriminals. An attack on the communication network could sever the connection between the OCC and the field elements or onboard systems, leading to loss of control and potential accidents.
Lets dwelve into two examples of possible attack vectors that we are concerned about in any railway network.
Insider Threats: A Growing Concern
Unlike external attackers who must breach network defenses to access critical systems, insiders—whether they are employees, contractors, or third-party vendors—already have legitimate access to the network. This access, combined with their knowledge of internal systems and processes, makes insider threats both difficult to detect and potentially devastating.
Types of Insider Threats
Insider threats in the railway industry can manifest in several ways:
- Malicious Insiders: These individuals intentionally misuse their access to cause harm. Motivations can range from personal grievances, financial gain, or ideological reasons. For example, a disgruntled employee might plant malicious software in the network, or a compromised contractor could intentionally alter critical settings within the signaling system.
- Inadvertent Insiders: Not all insider threats are intentional. Employees may inadvertently cause security breaches through negligence, such as by falling victim to phishing attacks or by connecting insecure devices to the network. An engineer using an infected USB drive to update a system could unknowingly introduce malware into the network, leading to widespread disruptions.
- Compromised Insiders: These are insiders who have been coerced or manipulated by external actors. This could involve a vendor technician whose credentials are stolen and used by hackers to gain access to the railway’s operational technology (OT) systems. In other cases, employees might be blackmailed or bribed to provide access to critical systems.
The Risks Posed by Insider Threats
The risks associated with insider threats are particularly high in the railway industry due to the critical nature of its operations:
- Access to Critical Systems: Insiders often have access to sensitive areas of the railway network, including control systems, signaling equipment, and communication networks. A compromised insider could disrupt train operations, manipulate signaling systems, or disable safety mechanisms, leading to potentially catastrophic outcomes.
- Difficulty in Detection: Unlike external threats, which often involve unusual network activity or attempts to bypass security measures, insider threats can be much harder to detect. Insiders may use their legitimate access to carry out harmful actions that do not immediately raise red flags. This makes traditional security measures, such as firewalls and intrusion detection systems, less effective against insider threats.
- Potential for Widespread Impact: The interconnected nature of railway systems means that an insider threat could have widespread consequences. For example, an insider who disrupts a signaling system could cause delays across the entire network, resulting in significant financial losses and endangering passenger safety.
Examples of Insider Threat Scenarios
- Remote Maintenance and Support: Modern railway systems often rely on remote access for maintenance and support. Technicians and engineers, often working for third-party vendors, need to access the network to perform updates and repairs. However, if a technician’s laptop is compromised—whether through malware or stolen credentials—attackers can use it as a gateway into the railway’s OT systems. This kind of insider threat is particularly concerning because it combines the need for legitimate access with the potential for significant harm.
- Unauthorized Use of Portable Media: In many cases, railway systems are protected by air gaps, where critical systems are isolated from external networks. However, insiders with physical access to these systems can bypass these protections. For instance, an employee inserting an infected USB stick into a workstation at an Operations Control Center (OCC) could introduce ransomware into the network. Given the reliance on legacy systems that are often difficult to patch, recovering from such an attack could be extremely challenging.
- Intentional Sabotage: An insider with malicious intent could directly sabotage railway operations. This could involve altering the programming of signaling equipment, disabling safety systems, or corrupting critical data. Given the complexity and scale of railway networks, even a small act of sabotage could have far-reaching consequences, including derailments, collisions, or widespread service disruptions.
Mitigation Strategies
Addressing insider threats requires a multi-faceted approach that combines technological solutions with organizational policies:
- Strict Access Controls: Limiting access to sensitive systems is crucial. Role-based access control (RBAC) can ensure that employees only have access to the systems they need to perform their jobs. Additionally, implementing the principle of least privilege (POLP) minimizes the risk of insiders having unnecessary access to critical systems.
- Continuous Monitoring and Behavioral Analytics: Advanced monitoring tools can detect unusual behavior by insiders, such as accessing systems at odd hours or attempting to move laterally across the network. Behavioral analytics can help identify patterns that deviate from the norm, allowing for early detection of potential threats.
- Regular Training and Awareness Programs: Educating employees about the risks of insider threats and proper cybersecurity practices is essential. This includes training on how to recognize phishing attempts, the dangers of using unauthorized devices, and the importance of reporting suspicious activity.
- Vendor Management and Security Protocols: Railway operators should establish strict security protocols for third-party vendors, including background checks, regular security audits, and clear guidelines for remote access. Ensuring that vendors comply with these protocols can significantly reduce the risk of insider threats originating from third-party sources.
- Incident Response Plans: Developing and regularly updating incident response plans that specifically address insider threats is crucial. These plans should include steps for quickly isolating affected systems, conducting forensic investigations, and restoring operations.
Advanced Attack Scenarios: Traffic Manipulation
Traffic manipulation attacks are among the most dangerous types of cyber threats because they can directly impact the physical safety of railway operations, potentially leading to catastrophic outcomes such as collisions, derailments, or severe service disruptions. This section delves into the mechanisms, risks, and implications of such attacks.
Understanding Traffic Manipulation Attacks
Traffic manipulation in the context of railway systems involves unauthorized interference with the signals, control messages, and communication protocols that govern train movements. These attacks can be executed in several ways:
- Signal Interference: Attackers may manipulate the signaling system to send incorrect signals to trains. For example, a green light (indicating it is safe to proceed) could be changed to red (stop), or vice versa, causing trains to stop abruptly or proceed when they should not. This can lead to severe disruptions, including potential collisions.
- Manipulation of Movement Authorities (MAs): In automated railway systems, trains operate based on Movement Authorities, which are messages that dictate the speed and distance a train can travel on a particular section of track. If attackers gain access to these messages, they could alter the instructions sent to the trains. For example, they could instruct a train to travel at high speeds on a section of track where it should be slow, leading to derailments or other dangerous situations.
- Network Spoofing: Attackers might introduce false data into the communication network, tricking the system into thinking there are trains on certain tracks when there are none, or vice versa. This could cause the system to reroute trains inappropriately, leading to gridlocks or unsafe conditions.
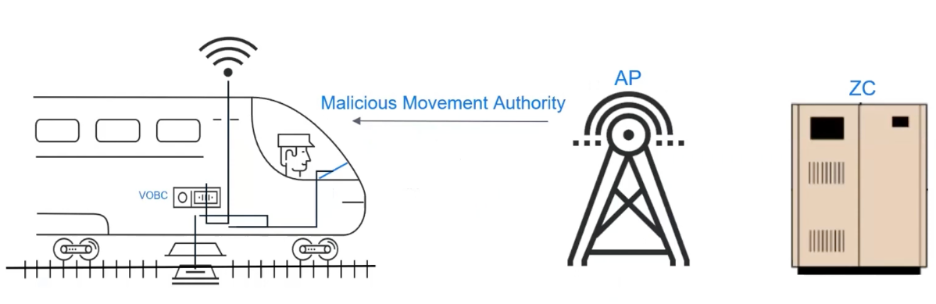
The Risks and Implications of Traffic Manipulation
Traffic manipulation attacks pose significant risks due to their potential to directly impact the safety and efficiency of railway operations:
- Physical Safety Threats: The most severe consequence of traffic manipulation is the risk of collisions or derailments. By altering signals or Movement Authorities, attackers could cause two trains to be on the same track section simultaneously, leading to a collision. In highly automated systems where human oversight is minimal, such attacks could be particularly devastating.
- Operational Disruption: Even if no physical harm occurs, traffic manipulation can cause massive operational disruptions. Trains may be forced to stop unexpectedly, schedules could be thrown off, and the overall efficiency of the railway network could be severely compromised. This not only impacts passenger services but can also disrupt freight operations, leading to significant economic losses.
- Psychological and Economic Impact: Beyond the immediate physical risks, successful traffic manipulation attacks can have broader psychological and economic consequences. Public trust in the safety of the railway system could be eroded, leading to reduced ridership and financial losses for operators. Moreover, such attacks could be part of a broader strategy in geopolitical conflicts to weaken a nation’s infrastructure and economy.
Mitigating Traffic Manipulation Risks
Given the severity of traffic manipulation attacks, mitigating these risks requires a comprehensive approach:
- Robust Authentication and Encryption: Ensuring that all communication between the OCC, trains, and trackside equipment is authenticated and encrypted is crucial. This prevents attackers from spoofing signals or injecting false data into the network.
- Network Segmentation and Isolation: Segmentation of the railway network, especially between IT and OT systems, can limit the spread of an attack. Isolating critical control systems from less secure networks reduces the risk of unauthorized access.
- Advanced Threat Detection: Deploying advanced intrusion detection systems (IDS) and anomaly detection tools can help identify unusual patterns in network traffic that might indicate an ongoing manipulation attempt. These systems should be capable of real-time monitoring and immediate response to potential threats.
- Redundancy and Fail-Safe Mechanisms: Implementing redundant systems and fail-safe mechanisms can mitigate the impact of a traffic manipulation attack. For example, if a signal is compromised, the system should default to a safe state, such as bringing trains to a controlled stop rather than allowing them to continue on a potentially dangerous path.
- Training and Preparedness: Regular training exercises that simulate traffic manipulation scenarios can help railway operators and staff respond effectively to real-world attacks. Being prepared can significantly reduce the time it takes to detect, contain, and mitigate an attack, thereby minimizing its impact.
Railway Cybersecurity: A Special Case
Railway cybersecurity stands apart from traditional IT security challenges due to the unique operational environment, specialized technologies, and the critical importance of safety in railway systems. Unlike typical IT environments, railway systems are deeply intertwined with physical operations, where the consequences of a cyberattack can be not just data loss but catastrophic accidents that endanger lives. This section explores the distinct aspects that make railway cybersecurity a special case and the implications for securing these vital infrastructures.
Special
- Geographically Distributed
- Diverse Communication Channels
- Multiple touchpoints with other infrastructure (roads, bridges, airports, etc..)
- Moving Fleets
Technological
- Multi-vendor complexity
- Proprietary Protocols
- Designed for Safety, not for Security
- Fail-safe mechanism
- Dynamic coupling
Operational
- Multiple Safety Levels
- Legacy & Obsolete Systems
- Delayed Software Updates
The Unique Operational Environment
Railway systems operate over vast geographic areas, often spanning entire countries or regions. This extensive distribution of assets introduces several challenges:
- Geographical Dispersion: Railway networks are spread across hundreds or even thousands of kilometers, with assets located in remote or difficult-to-access areas. This dispersion makes it challenging to implement and maintain consistent security measures across the entire network. For instance, trackside equipment and sensors may be located far from central control centers, making them vulnerable to both physical and cyber threats.
- Mobility of Assets: Unlike static IT environments, railway systems involve moving assets, such as trains, that interact dynamically with the network. A security solution that works for stationary systems may not be suitable for an environment where critical components are constantly on the move. For example, securing a computer on a moving train presents challenges in terms of maintaining consistent communication and updating software without interrupting operations.
- Real-Time Requirements: Railway operations are highly dependent on real-time data and control. Delays or interruptions in communication between trains and control centers can lead to dangerous situations. This real-time nature requires cybersecurity solutions that can operate without causing latency or disruption to critical operations.
Specialized Technologies and Protocols
Railway systems use a range of specialized technologies that are not commonly found in other industries:
- Proprietary Protocols: Many railway systems rely on proprietary communication protocols that were designed with safety in mind, rather than security. For example, signaling systems may use unique protocols that are optimized for reliable and fast communication but lack robust security features such as encryption. While the use of proprietary protocols can sometimes provide a degree of security through obscurity, it also means that cybersecurity solutions must be specifically tailored to these environments.
- Multi-Vendor Ecosystem: Railway systems often incorporate technologies from multiple vendors, each with its own proprietary systems and protocols. This diversity can lead to compatibility issues and makes it difficult to implement uniform security measures across the entire network. Moreover, managing security in a multi-vendor environment requires a deep understanding of each system’s specific vulnerabilities and how they interact within the larger network.
- Legacy Systems: Many railway systems still rely on legacy technologies that were not designed with modern cybersecurity threats in mind. These older systems are often critical to operations, such as signaling and interlocking systems, and cannot be easily replaced or updated due to the rigorous safety certifications required. As a result, these systems are particularly vulnerable to cyberattacks, and securing them requires innovative approaches that do not compromise safety.
The Intersection of Safety and Security
Safety is the paramount concern in the railway industry, and it influences how cybersecurity measures are implemented:
- Safety-First Design: Railway systems are traditionally designed with safety as the primary consideration, which can sometimes conflict with cybersecurity practices. For example, safety protocols in railways often prioritize open and clear communication to ensure that emergency signals are received without delay. However, this openness can also make the systems more vulnerable to interception or manipulation by attackers.
- Safety Standards vs. Security Protocols: Many railway systems are governed by stringent safety standards, such as Safety Integrity Levels (SIL) for signaling equipment. These standards ensure that systems perform reliably under all conditions, but they can also restrict the implementation of certain cybersecurity measures. For instance, updating software on a SIL-certified system may require extensive re-certification, which is time-consuming and costly. As a result, security patches may be delayed or avoided altogether, leaving the system vulnerable.
- Balancing Act: The challenge in railway cybersecurity is finding the right balance between maintaining the high safety standards that protect passengers and ensuring robust cybersecurity measures that protect against digital threats. This balance requires close collaboration between safety engineers and cybersecurity experts to develop solutions that do not compromise one for the other.
The Role of Human Factors
Human factors play a significant role in railway cybersecurity, both as a potential vulnerability and as a critical component of a robust security strategy:
- Training and Awareness: Railway staff, including engineers, operators, and maintenance personnel, must be trained to recognize and respond to cybersecurity threats. However, the specialized nature of railway systems means that standard IT cybersecurity training may not be sufficient. Staff need training that is tailored to the specific technologies and risks present in the railway environment.
- Operational Constraints: In a high-stakes environment like railways, where delays can have serious safety implications, there may be a reluctance to implement security measures that could slow down operations. This can lead to situations where security best practices are bypassed in the interest of maintaining operational efficiency, creating vulnerabilities that could be exploited by attackers.
- Insider Threats: As discussed earlier, insider threats are a significant concern in the railway industry. The combination of extensive system access and specialized knowledge makes insiders uniquely positioned to cause harm, whether intentionally or accidentally. Mitigating this risk requires a combination of technical controls, such as access management, and organizational measures, such as thorough background checks and ongoing monitoring of employee behavior.
IT vs. OT vs. Rail-OT: Understanding the Differences
In the world of cybersecurity, understanding the distinctions between Information Technology (IT), Operational Technology (OT), and Rail-OT is crucial for effectively protecting railway systems. While IT and OT have been widely discussed in cybersecurity contexts, Rail-OT presents unique challenges and requirements due to the specialized nature of railway systems.
IT Security
- Standard IP based protocols (e.g, TCP/IP, HTTP)
- Non-deterministic behavioral analytics (humans)
- Active vulnerability scanning OK
- Regular patching & OS updates are encouraged
OT Security
- Standard & proprietary industry protocols (e.g, GE SRTP, Siemens S7)
- Deterministic behavioral analytics (machine-to-machine)
- Active scanning creates downtime
- Patching creates downtime & OS updates force SCADA application re-writes
Rail-OT Security
- Railway proprietary/unique protocols (e.g, Interlocking, ETCS, SCI, MVB)
- Behavior determined by Railway Logic
- Downtime by scanning or patching is not tolerated
- Patching is harder than in other industrial networks
- Multi-vendor environment with a geographically- spread network
Information Technology (IT)
IT encompasses the use of computers, networks, storage, and other physical devices to process, store, and transmit data. In typical corporate environments, IT systems support business operations, such as email, financial transactions, and data management. IT cybersecurity focuses on protecting data confidentiality, integrity, and availability against threats such as data breaches, ransomware, and phishing attacks.
Key characteristics of IT systems include:
- Data-centric: IT systems prioritize the security of digital information, focusing on protecting against unauthorized access, data loss, and other forms of cyber threats.
- Standard Protocols: IT systems typically use widely adopted protocols, such as TCP/IP, HTTP, and others, which are standardized and well-understood in the cybersecurity community.
- Patch Management: Regular software updates and patches are a standard practice in IT to address vulnerabilities and enhance security.
Operational Technology (OT)
OT refers to hardware and software that detects or causes changes through direct monitoring and control of physical devices, processes, and events in an industrial environment. OT is commonly found in sectors such as manufacturing, energy, and transportation, where it controls critical infrastructure.
Key characteristics of OT systems include:
- Safety-Centric: OT systems prioritize the safety and reliability of physical processes, with cybersecurity often being a secondary consideration. This is because any failure in OT systems could result in physical harm, environmental damage, or operational shutdowns.
- Proprietary Protocols: OT systems often use proprietary protocols designed specifically for industrial processes. These protocols are typically less understood in the broader cybersecurity community, making it challenging to apply standard security solutions.
- Legacy Systems: Many OT systems are based on older technologies that were not designed with cybersecurity in mind. These systems are often difficult to update or replace due to the critical nature of the operations they support.
Rail-OT: A Specialized Domain
Rail-OT represents a specialized subset of OT systems that are used in the railway industry. These systems are integral to the operation of trains, including signaling, control, and communication systems that ensure the safe and efficient movement of trains.
Key characteristics of Rail-OT systems include:
- Railway-Specific Protocols: Rail-OT systems often use unique, proprietary protocols that are specifically designed for railway operations. These protocols are tailored to the needs of the railway industry, prioritizing safety, timing, and reliability over general cybersecurity concerns.
- Safety Over Security: Similar to other OT systems, Rail-OT prioritizes safety, sometimes at the expense of cybersecurity. For instance, many Rail-OT systems avoid encryption to ensure that communication is open and transparent, which is vital for safety but leaves systems vulnerable to cyber threats.
- Operational Constraints: Rail-OT systems must operate in real-time, with minimal tolerance for delays or errors. This real-time requirement complicates the application of traditional cybersecurity measures, which may introduce latency or require system downtime for updates.
The Intersection and Challenges
The challenge in securing railway systems lies in the intersection of IT, OT, and Rail-OT. Each domain has its own requirements, protocols, and vulnerabilities, making a one-size-fits-all approach to cybersecurity ineffective. Instead, cybersecurity strategies must be tailored to address the specific needs of each domain while ensuring that they work together cohesively.
- Integration of IT and OT: As railway systems become more connected, the integration of IT and OT systems increases the potential attack surface. Cyber threats that originate in IT environments can spread to OT and Rail-OT systems, where they may cause physical damage or operational disruptions.
- Specialized Expertise Required: Securing Rail-OT systems requires expertise that goes beyond traditional IT or OT cybersecurity. Professionals in this field must understand the unique protocols and safety requirements of railway systems, as well as the operational constraints that limit the application of standard cybersecurity measures.
- Balancing Safety and Security: One of the biggest challenges in Rail-OT cybersecurity is balancing the need for security with the uncompromising demands of safety. Any cybersecurity measure must be carefully evaluated to ensure that it does not interfere with the safe operation of trains.
Global Standards and Regulations: Safeguarding the Future of Railway Cybersecurity
As cyber threats to railway systems have escalated, so too has the need for stringent global standards and regulations to ensure the security of these critical infrastructures. These standards and regulations are designed to address the unique challenges faced by railway operators, combining the principles of safety and security into a cohesive framework. However, implementing these standards in the complex, real-world environment of railway operations requires a nuanced understanding of both the regulations themselves and the specific needs of the railway industry.
The Evolution of Railway Cybersecurity Standards
The railway industry has traditionally focused on safety, with standards and practices aimed at preventing accidents and ensuring the reliable operation of trains. However, as railways have become more digitized, the need for cybersecurity has become increasingly apparent. This has led to the development of new standards that integrate cybersecurity into the broader framework of railway safety and reliability.
- IEC 62443: One of the foundational standards for cybersecurity in industrial control systems (ICS), including those used in railways, is IEC 62443. This standard provides guidelines for assessing and managing cybersecurity risks in ICS environments, emphasizing the need for a defense-in-depth approach. While IEC 62443 is not specific to railways, it forms the basis for many of the cybersecurity practices adopted in the industry.
- CENELEC TS 50701: Recognizing the need for a railway-specific cybersecurity framework, the European Committee for Electrotechnical Standardization (CENELEC) developed TS 50701. This technical specification is an adaptation of IEC 62443 tailored to the railway sector. It combines cybersecurity requirements with the established safety standards in the railway industry, such as RAMS (Reliability, Availability, Maintainability, and Safety). TS 50701 provides a structured approach to assessing and mitigating cybersecurity risks in railway systems, ensuring that both safety and security are maintained.
- Upcoming IEC 63452: The upcoming IEC 63452 standard is set to further refine the cybersecurity framework for railways. This standard aims to integrate the principles of IEC 62443 and TS 50701, providing a comprehensive set of guidelines that address the unique challenges of railway cybersecurity on a global scale. IEC 63452 will be a significant milestone in the industry’s efforts to protect its critical infrastructure from cyber threats.
Regional and National Regulations
In addition to global standards, various regional and national regulations have been introduced to enhance cybersecurity in the railway sector. These regulations often reflect the specific needs and threat landscapes of different regions, providing additional layers of protection.
- NIS2 Directive (Europe): In Europe, the NIS2 Directive is a key regulation that impacts railway cybersecurity. This directive mandates that operators of essential services, including railways, implement robust cybersecurity measures and report significant incidents to the relevant authorities. NIS2 builds on the original NIS Directive by expanding the scope of regulated sectors and introducing stricter requirements for risk management and incident reporting.
- TSA Directives (United States): In the United States, the Transportation Security Administration (TSA) has issued directives aimed at improving the cybersecurity of critical transportation infrastructure, including railways. These directives focus on network segmentation, incident detection, and the reporting of cybersecurity incidents. They represent a significant step towards ensuring that railway operators in the U.S. are prepared to defend against evolving cyber threats.
- National Cybersecurity Strategies (India): In India, the government has implemented a National Cybersecurity Strategy that includes specific provisions for protecting critical infrastructure, such as railways. The Indian Railways, in collaboration with the National Critical Information Infrastructure Protection Centre (NCIIPC) and CERT-In, has developed guidelines and frameworks to secure its operations. These efforts are part of a broader strategy to enhance the resilience of India’s critical infrastructure against cyberattacks.
Safety Critical OT Networks in Indian Railways – case study
Indian Railways has identified several critical Operational Technology (OT) networks that are vital to the safe and efficient operation of its extensive railway network. These networks are categorized under three primary areas: Critical Information Infrastructure, Indian Railways Signal Manual, and Indian Railways Telecom Manual. Below is an overview of the key components and requirements outlined for each category.
Critical Information Infrastructure – “Protected Systems”
This category includes the most essential systems that ensure the operational continuity and safety of Indian Railways. These systems are classified as protected under critical information infrastructure, highlighting their importance in maintaining national security and public safety. The list includes:
- Passenger Reservation System: The backbone for managing bookings and reservations, ensuring passengers can plan their journeys effectively.
- Freight Operations Information System: Manages the logistics of freight transport, crucial for the economic efficiency of the railway network.
- Electrical SCADA: Supervisory control and data acquisition systems for managing and monitoring electrical networks, vital for the safe operation of trains.
- Centralized Traffic Control: Controls train movements across the network, preventing collisions and optimizing traffic flow.
- Train Management System: Ensures the smooth operation of trains by coordinating scheduling, routing, and real-time monitoring.
- Train Collision Avoidance System (KAVACH) – Signaling: A critical safety system designed to prevent train collisions through automatic signaling.
- Rolling Stock Systems (TCMS, PIS, onboard WiFi networks): These include Train Control and Management Systems (TCMS), Passenger Information Systems (PIS), and onboard WiFi networks that are essential for both safety and passenger convenience.
Indian Railways Signal Manual – 2021
The Indian Railways Signal Manual lays out specific requirements and guidelines for the secure and reliable operation of signaling systems. Key sections include:
- 11.1.5 Network Requirements: This section outlines the necessary network infrastructure, including security requirements, to ensure robust and resilient communication within the signaling systems.
- 13.4.10 Data Communication Network: Focuses on the communication protocols and data transfer requirements between different signaling components, ensuring that information is accurately and securely transmitted.
- 21.4.3 Interface with Electronic Interlocking: Details the interface requirements for electronic interlocking systems, which are crucial for preventing conflicting train movements.
- 22.1.1 Requirements of Signalling: Specifies the overall signaling requirements, ensuring that all signals are correctly configured and maintained to prevent accidents and ensure smooth railway operations.
Indian Railways Telecom Manual – 2021
The Telecom Manual sets the standards for communication networks within Indian Railways, emphasizing the importance of secure and reliable telecommunications for railway operations. Key sections include:
- 15.2.2 Railway Networks: Details the specific requirements for railway communication networks, ensuring they are resilient against cyber threats and capable of supporting the operational needs of Indian Railways.
- 15.9 Intrusion Prevention System (IPS)/Intrusion Detection System (IDS): Specifies the implementation of IPS and IDS to protect against unauthorized access and detect potential security breaches within the network.
- 15.10.2 Network Protection, Intrusion Detection, and Intrusion Prevention: Outlines comprehensive strategies for protecting the network, including the deployment of systems to detect and prevent intrusions, ensuring the security and integrity of critical railway operations.
Challenges in Implementing Standards and Regulations
While the development of global standards and regulations is a crucial step towards enhancing railway cybersecurity, implementing these guidelines in practice presents several challenges:
- Compliance vs. Practicality: Railway operators must balance the need for compliance with the practicalities of maintaining and operating a complex, real-time transportation system. For example, updating legacy systems to meet modern cybersecurity standards can be a time-consuming and costly process, particularly when these systems are critical to daily operations.
- Integration with Safety Standards: As discussed earlier, the integration of cybersecurity with existing safety standards is essential but challenging. Railway systems are designed with safety as the top priority, and introducing new cybersecurity measures must not compromise these safety standards. This requires careful coordination between safety engineers and cybersecurity experts to ensure that both safety and security are addressed effectively.
- Resource Constraints: Implementing comprehensive cybersecurity measures across a vast and geographically dispersed railway network requires significant resources, both in terms of technology and expertise. Smaller railway operators, in particular, may struggle to allocate the necessary resources to achieve full compliance with global standards and regulations.
The Way Forward
As the threat landscape continues to evolve, so too must the standards and regulations that govern railway cybersecurity. Future developments in this area will likely focus on:
- Harmonization of Standards: Efforts to harmonize global standards, such as the alignment between IEC 62443, TS 50701, and the upcoming IEC 63452, will help create a more cohesive framework for railway cybersecurity. This will make it easier for operators to implement consistent security measures across different regions and comply with multiple regulatory requirements.
- Advanced Threat Mitigation: As cyber threats become more sophisticated, the standards and regulations governing railway cybersecurity will need to evolve accordingly. This may include the development of new guidelines for emerging technologies, such as artificial intelligence and machine learning, which can play a role in detecting and mitigating advanced threats.
- Increased Collaboration: International collaboration between regulatory bodies, railway operators, and cybersecurity experts will be essential in developing and refining standards and regulations. Sharing knowledge and best practices across borders will help the industry stay ahead of emerging threats and ensure the safety and security of global railway networks.
Summary: Essential Cybersecurity Takeaways for Railway Systems
As railway systems increasingly adopt digital technologies, cybersecurity becomes an essential component of ensuring safe and reliable operations. Here are some key takeaways that every railway operator and stakeholder should consider when developing and implementing cybersecurity strategies.
- Proactive Security Design is Crucial – Railway systems are not inherently secure unless they are actively designed and regularly checked for vulnerabilities. Relying on assumptions can lead to significant security gaps. It is essential to ensure that all components of the railway network, from signaling systems to communication networks, are built with security in mind and undergo continuous monitoring and testing.
- Prepare for Regulatory Requirements – Cybersecurity regulations are becoming more stringent worldwide, and waiting for them to catch up with your operations could leave you vulnerable. Railway operators should not wait for mandatory requirements to take action. Instead, they should proactively prepare by implementing robust cybersecurity measures that align with or exceed existing standards.
- Tailored Cyber Solutions for Railway Technologies – Railway technologies have unique operational requirements, and applying generic cybersecurity solutions may not be effective. It’s important to implement cybersecurity measures that are specifically designed to address the challenges faced by railway systems, ensuring that the right solutions are applied in the right places to protect critical infrastructure.
- OT Cybersecurity Requires Dedicated Expertise – Operational Technology (OT) cybersecurity is different from traditional IT security and requires specialized expertise. OT systems are integral to the safe operation of trains, and securing these systems demands knowledge of both cybersecurity principles and the specific operational requirements of railway environments. Ensuring that your team has access to dedicated OT cybersecurity experts is crucial for maintaining security.
- The Myth of Closed Loop and Air-Gapped Networks – The idea that closed loop networks or air-gapped systems are completely secure is a myth. Even supposedly isolated networks can be vulnerable to cyber threats through insider attacks, compromised devices, or sophisticated attack vectors. Railway operators must remain vigilant and implement additional layers of security to protect against these potential vulnerabilities.
- Cybersecurity Goes Beyond Products—Start Planning Today – Effective cybersecurity is not just about purchasing the latest security products. It requires comprehensive planning, including the development of a security strategy, risk assessments, incident response plans, and ongoing training for staff. Start your cybersecurity planning today to build a resilient and secure railway network.
By incorporating these takeaways into their cybersecurity strategies, railway operators can better protect their networks from emerging threats, ensure compliance with regulations, and maintain the safety and reliability of their operations.
Disclaimer:
- The views expressed in this post are my own and do not necessarily reflect the views or positions of my organization.
- The names and designations of individuals mentioned in this blog have been changed to protect their privacy. Any resemblance to real persons, living or dead, is purely coincidental. The content and quotes provided are intended for illustrative purposes only and are based on common industry experiences and challenges.
