Industrial Grade Secure Remote Operations - Part-1

Business continuity remains a strategic priority, as new worldwide complexities and uncertainties arise. A March 2020 Forrester report notes that provisioning employees with remote access technologies is a key continuity strategy at 88 percent of organizations surveyed, while Gartner recommends to “accelerate the development of a technology infrastructure that can support alternative types of working.”
Companies looking to empower employees, contractors & 3rd parties to access corporate data and applications wherever they are working have traditionally used a Remote Access Solution and opened access to their corporate network to anyone who had the credentials of an authorized user. It is this simplicity and exposure that inherently brings risk to a company’s intellectual property, and organisations have spent years trying to mitigate this risk in a multitude of ways, mostly by adding to the already large stack of security appliances at their gateway. This solution is both complex and costly.
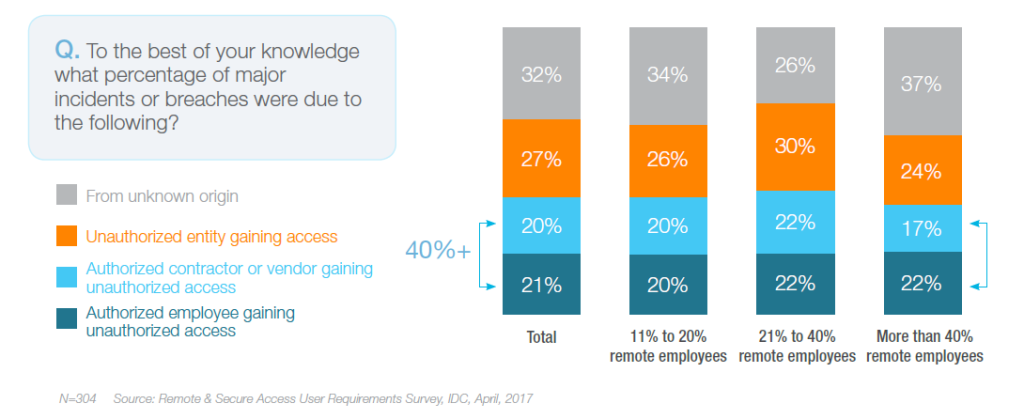
Source: An IDC InfoBrief, Sponsored by Akamai | September 2017
A survey conducted by IDC in September 2017 revealed that more than 40% of the breaches come from authorized users accessing unauthorized systems. 50% + report they use more than 10 network and application components to add a new external user group to an organization. While the survey revealed VPN and Cloud tools are favoured most by IT and Line of Business, VPN is also linked to companies that have the highest number of major incidents from authorized and unauthorized employees, contractors and vendors gaining access in this survey.
Cyber attackers are responding faster and becoming more agile and what has been observed as a pattern is that when a vulnerability is released, sometimes its preceded or shortly after the vulnerability is released with activities, tools and exploit modules and proof-of-concept codes. It is also often seen that a few attack data start to appear soon after a vulnerability is disclosed, remote access protocols and technologies are of high value since they allow getting into an environment. In addition to this, even after the patches are available because it takes time to deploy in a production environment, there is period after the patch is available when cyber exploits can occur. So, you need to be very aware of the risk of the attack and ensuring that system remains patched at all times.
Businesses must pivot from the common security mantra of “trust but verify” to “verify and never trust” in the new threat landscape. Traditional access solutions grant users full access to the network once they “verify” through user credentials, but is that the most secure approach? Solutions like VPNs put a hole through your firewall, enabling anyone inside of your perimeter to potentially move laterally across your network.
Use Cases for Enterprise-Grade Secure Remote Access
It is estimated that at least a 35% efficiency gain can be achieved through automation, and improvements in cybersecurity risk management can help mitigate an estimated $75M in cyber-attack damage. Automated discovery and inventory of IT assets alone can reduce labour costs by approximately $200,000 a year, depending on organization size, location and asset composition. In business continuity situations, the benefits of secure remote access technology become immeasurable because you are keeping operations running, even with limited staff or no local staff.
The uptime of facilities processing or producing goods and services is constantly impacted, whether by market, technical, human or other conditions that continually change. An essential component of a robust IT architecture is the ability to connect to operating assets, whether on site or remotely. This capability is especially useful to operating personnel, who bear the burden of actively managing and/or using the assets day in and day out, yet who are frequently short-staffed and tasked with a wide range of work responsibilities. The same person accountable for cybersecurity may also be called on for updating standard operating procedures and for managing budget and staff planning, for example.
Use cases for enterprise-grade secure remote access can include:
Exploitation of Connectivity
Cybersecurity is an on-going concern that affects remote operations as malicious actors leverage unmanaged or poorly monitored connection points. Secure remote access solutions that centralize and control activities at a granular level can help mitigate risk of this exploitation. Closely controlling and monitoring connections, together with logs and recorded sessions, can help with cybersecurity threat mitigation as well as compliance.
Particularly in times of crisis, hackers’ prey on panic and human emotions. They deploy social engineering efforts and other scams that trick employees into allowing access or otherwise breaking security policies. Policies established and enforced through a secure remote access solution can raise alerts and automate actions to rapidly act on discovered threats or attempts at exploitation. Establishing secure remote access can also positively influence network segmentation, and related privileged access rights assigned to specific personnel. Together with solutions such as threat monitoring, these safeguards can increase the IT network’s resilience both short term and long term.
Centralized Operations
A common use case for enterprise grade secure remote access includes situations where operations have already been centralized across multiple sites, to improve cost efficiencies or offset the challenges of staffing offshore or isolated physical locations. In these cases, centralized solutions can help standardize how secure remote connections are managed across assets at any number of locations. Considering there could be dozens of technicians from multiple vendors maintaining a globally distributed IT environment on any given day, a centralized view into all connectivity helps tighten control and reduce inefficiencies. All requests are funneled through the same secure tunnel, including verification of the technician, session authorization by the local on-premise staff, and logging of the recorded session for oversight and staff training purposes. Rather than allowing the risky conditions of disparate and ad hoc verification of important system connectivity, IT leaders can unify and simplify oversight of remote connections.
Security Operations Centre
A growing use case is allowing a third-party Security Operations Center (SOC) provider, specific to operations, to handle all monitoring and maintenance across sites. This can increase mean-time-to-resolution by ensuring 24/7 access to expertise anywhere, as part of the service level agreement (SLA). For specialized skills such as IT cybersecurity threat monitoring, these services can expand bench strength while keeping operations up, especially amidst heightened threat levels. Considering the significant and high-impact of IT systems, an IT operations SOC can lend the required expertise as well as geographic coverage needed by many global enterprises. The SOC can typically manage multiple vendor technologies while providing regular monitoring and reporting for compliance needs if a capable solution is deployed.
Continued …..
