Quantum Computing and it's impact on Cybersecurity of legacy control systems

If someone tells you that they actually know Quantum Computing, you should not trust this person because nobody does.
In our current world, events unfold in a deterministic manner: an apple falls due to earth’s gravity, and the sum of 2 plus 2 is consistently 4. However, in the realm of quantum mechanics, reality operates on a probabilistic basis.
In the Quantum world, the equation 2 plus 2 doesn’t always result in 4. Instead, it equals 4 with a certain probability, and occasionally, it might equal 4 only when we are not looking.
What is Quantum Computing …?
Quantum computing represents a significant shift in the field of computation, using the principles of Quantum mechanics. To describe the difference between Quantum computing from classical computing, I highlight a few fundamental concepts here:
- Quantum Bits (Qubits): Qubits are the basic unit of quantum information, analogous to bits in classical computing. However, unlike classical bits that can be either 0 or 1, qubits can exist in a state of superposition, where they can be both 0 and 1 simultaneously. This property is fundamental to the power of quantum computing.
Superposition allows a single qubit to represent numerous possible combinations of 1 and 0 at the same time. This means that a quantum computer with n qubits can represent 2n states simultaneously. For example, while a classical computer with 3 bits can represent one of the 8 possible combinations at a time, a 3-qubit quantum computer can represent all 8 combinations simultaneously. Superposition enables quantum computers to perform a vast number of calculations in parallel, potentially solving certain problems much faster than classical computers.
- Entanglement: A pair of qubits can be generated that are “entangled,” which means the two members of a pair exist in a single quantum state. Changing the state of one of the qubits will instantaneously change the state of the other one in a predictable way. This happens even if they are separated by very long distances.
As per my research, nobody really knows quite how or why entanglement works. It even baffled Einstein, who famously described it as “spooky action at a distance.” But it’s key to the power of quantum computers. In a conventional computer, doubling the number of bits doubles its processing power. But thanks to entanglement, adding extra qubits to a quantum machine produces an exponential increase in its number-crunching ability. Entanglement allows for incredibly dense information encoding and has profound implications for information processing and transmission. It plays a critical role in quantum algorithms and quantum cryptography.
Quantum Gates: In quantum computing, operations are performed using quantum gates, which manipulate an input of qubits to produce an output. These gates are more complex than their classical counterparts. For example, common quantum gates include the Hadamard gate (creating superposition), Pauli-X, Y, and Z gates (bit-flip and phase-flip operations), and controlled gates like the CNOT gate (entangling two qubits). The complexity and capabilities of quantum gates allow for the construction of powerful quantum algorithms, like Shor’s algorithm for factoring large numbers and Grover’s algorithm for database searching.
Using very complex engineering, the superposition can be collapsed into an answer to your calculation.
How does a Quantum Computer look like …?
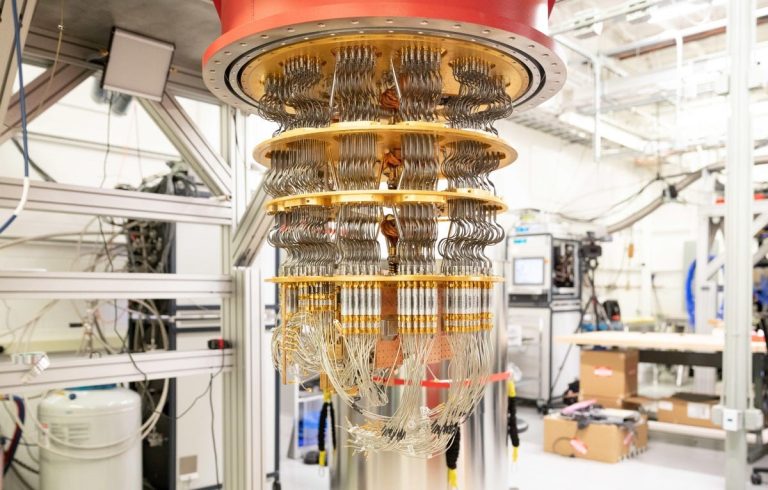
Picture credit – Take a look at Google’s quantum computing technology – CNET
The image displayed above shows a real quantum computer. Its central section, resembling a golden chandelier, is the compartment where the Qubits are located. The quantum computer in this image is not operational as it appears open. In another image below, a large cylinder is visible; this is crucial for maintaining the computer at an extremely low temperature, just a fraction above absolute zero. This cold environment is essential to prevent external energy from disturbing the highly sensitive Qubits, ensuring their precise manipulation and control.
At the top of the structure, you can observe pipes associated with cryogenics, a critical and complex aspect of successful quantum computing. Behind this setup lies a classical computing stack, integral to the quantum computing architecture. This classical stack is used to issue commands to the Qubits, such as initiating spin, managing their superposition states, and other operations, demonstrating the intricate interplay between classical and quantum computing systems.

Picture credit: Take a look at Google’s quantum computing technology – CNET
Thus, there are things that classical computers will have to do and things that quantum computing will have to do, so they will both coexist in the future.
While getting into more details of quantum computing is beyond the scope of this blog, here I wanted to very quickly introduce some key concepts before looking into their application. If you are interested in exploring more about quantum computing, please take a look at the references at the end.
Impact of Quantum computing on Legacy Control Systems
The advent of quantum computing will have profound impacts on legacy control systems in several areas. In this section, I especially look into the impact on the critical infrastructure in particular energy sector:
Cybersecurity: Quantum computers can potentially break many of the cryptographic algorithms currently used to secure data. This poses a significant risk to legacy systems relying on these algorithms. The solution is to transition to quantum-resistant cryptographic methods.
Data Processing: Quantum computers can process and analyse data much faster than classical computers. For control systems that handle large volumes of data, such as in the Smart Grid Management System quantum algorithms can help enhance the management of smart grids by processing vast amounts of data from sensors, smart meters, and IoT devices in real-time, leading to improved load balancing, demand forecasting, and real-time decision-making for energy distribution, leading to increased efficiency and reliability of the power grid. As part of Predictive Maintenance Application, quantum computing can be applied to analyse large datasets from equipment sensors to predict failures and maintenance needs, thereby preventing outages and costly repairs, extending the lifespan of equipment, and ensuring uninterrupted power supply.
Optimization Problems: Quantum computing has the potential to solve complex optimization problems more efficiently than classical computers. This can benefit the electric industry, where optimization is key. For example, Power Flow Optimization which would essentially optimize power flow in transmission networks to minimize losses and improve efficiency. Supply and Demand Balancing where Quantum algorithms can be used to match energy supply with demand in real-time, considering factors like renewable energy sources, storage capacities, and consumption patterns leading to better integration of renewable energy sources, reduction of waste, and lower energy costs.
Simulation and modeling: Quantum computers can simulate molecular and quantum mechanical systems more effectively than classical computers. One of the application could be in Grid Resilience Analysis by simulating and analysing grid behaviour under various stress scenarios, such as natural disasters or cyberattacks, thereby enhancing the ability to plan for and mitigate potential disruptions and ensuring a more resilient power grid. Renewable Energy Integration could be another potential application. Modeling complex interactions in a grid that includes high levels of renewable energy sources, which are variable and unpredictable, can assist in better understanding and management of renewable integration challenges, leading to more efficient use of green energy sources. Another potential application could be Electric Vehicle (EV) Charging Networks, by simulating and optimizing the deployment and operation of EV charging stations, we can ensure efficient energy use and minimize impacts on the power grid.
Upgrade and Compatibility Challenges: Integrating quantum computing capabilities into existing systems poses significant technical challenges. Legacy systems may need substantial upgrades or even complete redesigns to be compatible with quantum computing.
Skill Gap: The quantum computing field requires a different set of skills and knowledge. There is a growing need for education and training in quantum computing to manage and operate these advanced systems.
Quantum Computing impact on Cybersecurity
Quantum computing’s potential to revolutionize various aspects of technology is particularly notable in the field of cybersecurity. Here are some key examples of how quantum computing can impact cybersecurity:
Breaking Current Encryption Methods: Many of today’s encryption techniques, like RSA and ECC (Elliptic Curve Cryptography), rely on the difficulty of factoring large numbers or solving discrete logarithm problems, tasks that are computationally intensive for classical computers. However, quantum computers can solve these problems much more efficiently using algorithms like Shor’s algorithm, potentially rendering current encryption methods obsolete.
Enhanced Cryptanalysis: Quantum computing could significantly advance cryptanalysis—the practice of deciphering encrypted communications without the key. This advancement could enable the decryption of historically encrypted messages or data that was considered secure under classical computation standards.
Quantum Key Distribution (QKD): On the positive side, quantum computing introduces new methods of secure communication, such as QKD. QKD uses quantum mechanics to securely distribute encryption keys, with the advantage that any attempt to eavesdrop on the key distribution can be detected, thanks to the principles of quantum mechanics.
Threat to Blockchain and Cryptocurrencies: Blockchain technology and cryptocurrencies like Bitcoin rely heavily on cryptographic algorithms for securing transactions and mining processes. Quantum computing poses a significant threat to these systems as it can potentially break the cryptographic safeguards that protect wallets and transaction ledgers.
Increased Hacking Capabilities: State-sponsored and highly sophisticated hackers could use quantum computers to breach current security systems, accessing confidential data, disrupting critical infrastructure, and impacting national security.
Post-Quantum Cryptography (PQC): In response to these threats, there is a growing focus on developing PQC algorithms designed to be secure against both quantum and classical computers. The transition to PQC will be crucial for maintaining cybersecurity in the quantum era.
Retroactive Decryption Risk: Encrypted data that is safe today against classical computers could be at risk in the future. If sensitive data is recorded now, it could potentially be decrypted by quantum computers in the coming years, posing a long-term data confidentiality risk. This is also infamously called “Harvest Now Decrypt Later” attack.
Secure Communication Channels: Quantum computing could impact secure communication channels like VPNs (Virtual Private Networks) and secure browsing protocols, necessitating a revaluation and redesign of these technologies to ensure continued confidentiality and integrity of data.
Case study – Exploitation of Cryptographic Vulnerabilities
Modern-day cryptography relies heavily on the computational difficulty of certain mathematical problems. For instance, RSA encryption is based on the challenge of factoring large numbers, and ECC (Elliptic Curve Cryptography) depends on the difficulty of the elliptic curve discrete logarithm problem. Classical computers, even the most powerful ones, require an impractical amount of time to solve these problems, which is why these encryption methods are considered secure today (when RSA first came out, the computing time required to break an RSA private key was in the order of billions of years of continuous computing time).
Quantum computing changes this landscape dramatically. A quantum computer can solve these problems much more efficiently than classical computers. The most famous example is Shor’s algorithm, developed by mathematician Peter Shor in 1994. This algorithm allows a quantum computer to factor large numbers and compute discrete logarithms in polynomial time, which could break RSA and ECC encryption schemes.
The practical implications of this are profound:
Decryption of Encrypted Data: An attacker with access to a sufficiently powerful quantum computer could potentially decrypt data that was previously considered secure. This includes historical data that has been encrypted and stored.
Man-in-the-Middle Attacks: A quantum-enabled attacker could intercept and decrypt secure communications, which rely on these encryption techniques.
Digital Signature Forgery: Quantum computing could also compromise digital signatures, undermining the integrity and non-repudiation of digital communications and transactions.
How to address the Threat
Various organizations around the world are working hard to address the threat from Quantum computing. Researchers over the past several years have identified a Quantum-Safe encryption. According to the magazine The American Scientist, NIST has already identified 69 possible encryptions the agency calls “Post-Quantum Cryptography (PQC).” NIST is also planning to release Post-Quantum Cryptography Standard by 2024.
Post Quantum Cryptography (PQC) is essentially a classical solution; although there is quantum in the title, there is no quantum in the solution. In order to be quantum-resilient, classical computing devices may use PQC in the future.
Then there is quantum cryptography, which is essentially a technique based on quantum systems, leveraging them for random number generators or quantum key distribution.
Both of these methods have different infrastructure requirements, and both have their own methods of being quantum resilient.
Quantum Key Distribution (QKD) is another promising project that the industry has been trying to fine-tune. QKD employs the properties of quantum physics to securely transfer a quantum key between two endpoints. In the early stages of the project, fibre optic cable was the only means by which the key could be transmitted. However, a second method was developed by the Chicago based company Quantum Xchange that can transfer the key over the internet.
NIST has identified a seven-step process for organizations to prepare for post-quantum cryptography. There is a lot of emphasis on quantum hygiene, which starts by getting an inventory of the cryptography that the organization has on their system. What type of data is being held, how valuable it is, and what is that data connected to? Start to prioritize and create a transition plan. The organizations can increase the key length in the existing encryption that they are using; by doing so, they would not be quantum secure, but this would improve their cyber hygiene for quantum readiness.

Ref: Preparing for Post-Quantum Cryptography Infographic (dhs.gov)
There will be legacy systems for which this migration would not be possible and they would have to be mitigated by either replacing them or by implementing a defence-in-depth methodology.
Conclusion
In conclusion, the advent of quantum computing presents a transformative and challenging frontier in the field of technology. As we’ve explored, quantum computing operates on principles vastly different from classical computing, harnessing the perplexing phenomena of superposition, entanglement, and quantum gates. These principles enable quantum computers to perform complex calculations at unprecedented speeds, offering significant advancements but also posing substantial challenges, particularly in cybersecurity and legacy system compatibility.
Quantum computing’s potential to decrypt currently secure data, its implications for secure communications, and the threat it poses to existing cryptographic methods like RSA and ECC highlight the urgent need for quantum-resistant cryptographic techniques. The development of Post-Quantum Cryptography (PQC) and Quantum Key Distribution (QKD) are critical steps in preparing for this new era. Organizations must prioritize understanding and adapting to these changes, including upgrading legacy systems and addressing the emerging skill gap in quantum computing.
As we stand on the brink of this quantum revolution, it’s clear that while quantum computing holds immense promise for solving complex problems and advancing technology, it also necessitates a revaluation of our current systems and a proactive approach to cybersecurity and data protection. The journey into the quantum realm is not just about embracing new computational powers but also about preparing for the profound shifts in how we secure, process, and manage information in a quantum-enabled world.
References
- Nielsen, M. A., & Chuang, I. L. (2010). “Quantum Computation and Quantum Information.” Cambridge University Press.
- Rieffel, E., & Polak, W. (2011). “Quantum Computing: A Gentle Introduction.” MIT Press.
- Horodecki, R., Horodecki, P., Horodecki, M., & Horodecki, K. (2009). “Quantum entanglement.” Reviews of Modern Physics, 81(2), 865.
- Bennett, C. H., Brassard, G., & Ekert, A. K. (1992). “Quantum cryptography.” Scientific American, 267(4), 50-57.
- Barenco, A., Bennett, C. H., Cleve, R., DiVincenzo, D. P., Margolus, N., Shor, P., Sleator, T., Smolin, J. A., & Weinfurter, H. (1995). “Elementary gates for quantum computation.” Physical Review A, 52(5), 3457.
- Kitaev, A. Y., Shen, A., & Vyalyi, M. N. (2002). “Classical and Quantum Computation.” American Mathematical Society.
- Shor, P. W. (1994). “Algorithms for quantum computation: Discrete logarithms and factoring.” Proceedings 35th Annual Symposium on Foundations of Computer Science. IEEE.
- Bernstein, D. J., & Lange, T. (2017). “Post-quantum cryptography.” Nature, 549(7671), 188-194.
- National Institute of Standards and Technology (NIST). “Post-Quantum Cryptography.” NIST website.
Disclaimer: “The views expressed in this post are my own and do not necessarily reflect the views or positions of my organization.”
